The 7 Pillars of Data Protection
By Raj Soni
There are many questions regarding how to adequately protect data in our organizations and in all its forms (structured and unstructured data). At Adaptive Systems, we focus exclusively in Data Security and we help organizations protect their data and comply with data privacy regulations. In this article we’re going to talk about 7 Pillars of Data Protection and why they are so important to helping you protect your most sensitive data.
Data is the lifeblood of our digital economy especially given how integral the use of digital information and communication technologies have become to our daily lives. Adequately protecting data is now an imperative but security is achieved in layers and there is no one solution that will solve all your security concerns.
I’d like to quickly cover the two most common data types before we expand on how best to secure it. Data is typically stored in one of two categories: structured and unstructured.
Structured data is data that has been predefined and formatted to a set structure before being placed in data storage and is what we’re going to talk about in this blog. Unstructured data is data stored in its native format and comes in a myriad of file formats, including email, Word, Excel, PowerPoint, social media posts, presentations, chats, IoT sensor data, and satellite imagery. Protecting sensitive unstructured data from leaving an organization, via emails or web transfers, requires DLP controls, which we’re not going to cover in this article.
When we talk about the “7 pillars of Data Protection” we’re mainly going to address structured data that are typically stored within databases. Most end users interact with the application on their screen but very few “touch” a database and don’t really care how data is retrieved as long as they can use it. Most users also assume databases are tucked away in a subnet that is only accessible to a few people which isn’t always the case especially in cloud environments. A fact that is commonly overlooked is that databases leverage service accounts with elevated privileged and perpetual access to the data within it; so, we need to keep an eye on these service accounts to ensure they aren’t compromised. So now that we have established that we are going to talk about structured data today, let’s get to it. We will address securing unstructured data and how to prevent it from leaving your organization using DLP controls in another blog.
The 7 Pillars of Protection examines major controls required to effectively secure data in databases/data stores, reduce your risk of a data breach and comply with regulatory mandates like GDPR, CCPA & SOX (to name a few).
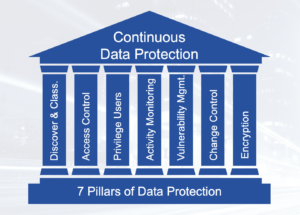
The Seven Pillars of Data Protection provide a holistic approach to securing data assets; especially given that together these key controls can help mitigate a variety of cyber threats with a potential to impact the confidentiality and/or integrity dimensions of data.
- Data Discovery & Classification
- Identity and Access Control
- Privileged Access Management
- Database Activity Monitoring (DAM)
- Vulnerability Management
- Change Management
- Encryption (for data-at-rest & data-in-transit)
Let’s dig a little deeper into each of these:
1. Discovery & Classification
Data is everywhere and getting a handle on it can seem overwhelming but “You can only protect what you know”! Data Classification can help identify where your sensitive data is. To be able to identify where all your data sources are and what kind of data is in each of these data sources sounds easy to do but is not so easy to accomplish. In many organizations, questions regarding Data Governance have to be established as a capability answered before a data classification exercise can even be discussed. There are many benefits to classifying data: it will help with data tagging, classifying can enable you to apply more precise rules to security policies, and it can help reduce or eliminate false positives. If you know where your data is you can apply more granular rules to your monitoring and encryption policies, you don’t have to monitor or encrypt everything, only what’s important; and this will help save time and money in the long run.
2. Identity and Access Controls
Access control is one of the four main controls leveraged for data protection. Data should only be shown to and be accessed by authorized users. So, it’s important to run database entitlement reports on a monthly basis for all of your data stores and validate that the DBAs and service accounts have authorized users.
3. Privileged Access Management
Databases not only have administrators (aka DBAs) with privileged credentials, but they also have service accounts that communicate with and retrieve data with privileged credentials. These need to be identified and incorporated into your organization’s security programs. Trust but verify. We want to make sure the privileged users are able to do their job but by identifying them and monitoring them you are verifying their credentials are not compromised by a third-party or a malware.
4. Activity Monitoring
Database Activity Monitoring (DAM) is an important control used for both regulatory compliance as well as security. Regulations like SOX require change management and access controls to be implemented, this can only be done if you are monitoring database activity with 3rd party tools or using techniques like native auditing provided across different database platforms. DAM can help you answer who, what, when, where, how and why. Please refer to our blog “Why Should I Monitor My Databases” where I go into a deeper discussion on security use cases for DAM.
5. Vulnerability Management
All too often we hear about security breaches that resulted from a known vulnerability being exploited. Most vulnerability management programs we see address only OS level vulnerabilities but to effectively protect data, database vulnerability scans need to be performed and identified issues addressed. There are specific database scanning tools such as IBM Guardium that scan not only version levels but go deeper than that to scan for patch level and verify default password changes.
Database vulnerability scans should be set up on a regular basis (monthly or quarterly based on business priorities and resource constraints) and remediation plans to address identified issues should be developed and tracked to completion.
6. Change Management
When someone asks, “what is the hardest thing in the universe?”, most people think of “diamonds”, but the real answer is “change”! Change is very hard to do and it’s ironic that change is the only thing in life that is constant! Change is inevitable and organizations are not immune to it either. So having an efficient change management process is very important. And for regulations like SOX, documenting changes and reconciling them with approvals is a core requirement.
7. Encryption (for both Data-at-rest and Data-in-motion)
Encryption is considered a technical data security control. Although it is not explicitly a GDPR requirement the regulation repeatedly highlights encryption and pseudonymization as “appropriate technical measures” for protecting PII (personally identifiable information). It’s also important to note that not everything needs to be encrypted, unless a specific regulation requires it. That’s why it’s important to go through a data classification exercise to know where your sensitive data is and encrypt only that.
So, there you have it – The 7 Pillars of Protection. I hope this was informative. If you have any questions or comments on what I presented please feel free to reach out to me. I love reading comments and feedback. Thank you!